
When is the right time to invest in a more robust vulnerability and patch management solution?
Patch management is an essential but increasingly expensive and time-consuming task for IT teams. Many companies have adopted automated patch deployment tools to make the process more efficient and meet compliance requirements. But the continuing dramatic growth in both the number and severity of vulnerabilities raises the question: when is it time to invest in more robust solutions to manage higher workloads, keep systems secure, maintain compliance and implement new technologies?
Short & sweet
- More and more companies are using automation tools to close security gaps
- The number of vulnerabilities has risen steadily in recent years
- The configuration of updates is a time-consuming task
- The ROI of patch management can be significantly improved with Managed Software
Over the past few years, many IT teams have replaced manual patch management procedures with commercial software tools that automate parts of the process.
The use of automation has expanded in response to the increasing number and severity of published CVEs and the complexity of business networks. It’s also been driven by
more frequent releases of patches by software vendors and the pressure on IT teams to address zero-day exploits quickly.
Most automation tools focus on patch deployment while some also are paired with solutions that provide continuous vulnerability monitoring. Both are in
line with recommendations from Gartner, Forrester, the SANS Institute and other industry experts. In fact, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) requires federal agencies to automate both
vulnerability management and patch deployment. Even without that guidance, most companies have come to realize that manual patch management is simply unsustainable.
Assessments vary, but the consensus is that automated tools for scheduling, deploying and monitoring patches can reduce IT time and effort by 30 to as much as 70 percent compared to
manual methods. Automation also can substantially reduce the number of days it takes IT teams to close vulnerabilities once they’re published -- the Mean Time To Remediate
(MTTR). Despite the broader use of automation, IT cybersecurity workloads continue to rise due to the growing complexity of IT environments and an increase
in the number and diversity of devices and applications.
A rising tide of vulnerabilities
The Ponemon Institute’s 2023 "The State of Patch Management in the Digital
Workplace" found that 65% of IT pros spend 10 to more than 25 hours per week deploying patches, or about 25% to roughly 70% of an IT team’s total monthly hours. The
demands of patch management are in addition to existing staff responsibilities for provisioning and maintaining endpoints, user support, working with vendors, updating IT inventories,
documenting compliance, and so on.
IT workloads have grown along with the number of vulnerabilities reported in NIST’s National
Vulnerability Database:
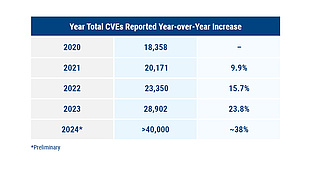
More than just deployment
Given the workloads and risks involved, automated patching is a necessity but it’s still just one step in the broader vulnerability management process. A more robust automated patch and vulnerability
management solution that’s integrated into day-to-day endpoint management practices can significantly reduce the time and effort needed to detect and close security gaps
while improving an organization’s compliance and cybersecurity posture.
Vulnerability management begins with an automatically updated inventory of all installed IT assets. Using that inventory data, an integrated vulnerability scanner can
automatically report security gaps such as system misconfigurations, outdated virus databases, unencrypted storage volumes, open network ports, missing OS updates and, of course, unpatched
systems.
A vulnerability scan can make it much easier to identify and prioritize needed patches. However, IT admins also must spend significant amounts of time testing and
configuring updates and patches to ensure compatibility and stability prior to deployment – a fact that was driven home by the faulty CrowdStrike update in July 2024. After deployment, IT admins must monitor
endpoints to ensure that update and patch installation was successful and did not introduce unexpected problems.
Update Management and Managed Software
IT security means keeping end devices up to date with updates. baramundi Update Management and Managed Software is at your side.
Find out how you can effectively eliminate vulnerabilities with
IT automation
Taking the next step
The baramundi Management Suite’s (bMS) provides solutions for automated inventory and software deployment. But it also offers the
capability to comprehensively automate vulnerability scanning, Windows update management, and patching of third-party applications with the bMS Vulnerability Scanner and Update Management and
Managed Software modules.
The Vulnerability Scanner automatically scans network endpoints for missing updates and patches, incorrect settings and other security gaps. It immediately shows
the presence and severity of vulnerabilities in a clear dashboard display along with recommended corrective actions. The Update Management module provides full
control over the timing and deployment of Windows client and server updates, i.e., no unexpected and possibly problematic automatic updates.
For patching third-party applications, the Managed Software module goes even further. It provides fully tested deployment-ready patch packages for more than 250
third-party applications. A dedicated team of experts at baramundi continuously monitors vulnerability databases for published CVEs as well as the availability of new patches
released by software vendors. The team thoroughly tests patches for stability and compatibility, then packages and seals them for secure distribution via the bMS. IT admins are notified
when new packages are ready so they can configure the parameters they require for their environments. Automated distribution using the bMS
Deploy module to target systems takes place when and how IT admins decide. Each of those capabilities is integrated in the bMS along with tools for regular endpoint
management.
ROI and improved infrastructure security
Using estimates from Gartner, the Ponemon Institute and other industry sources, we can provide an example of the ROI of using the Managed Software solution. For a basic
analysis, we’ll use the following conservative metrics for IT labor costs and time spent on vulnerability management activities (vulnerability/patch identification, testing, deployment and
monitoring) for a network with 500 to 1,000 endpoints:
IT labor costs
- National surveys in the U.S. show an IT admin salary range of $60,000 to $90,000/year or about $75,000/year or $6,250/month.
- 3 IT admins or $18,750/month
- A nominal 40-hour work week or 480 hours of total team time each month. (Real-world work weeks are likely much longer.)
Vulnerability management activities
For this analysis, we’ll assume that vulnerability scanning and patch deployment are automated while patch testing remains a mostly manual process. Accordingly:
- The IT team spends about 240 hours or about half of total team hours per month on patching-related work.
- Patch testing and validation typically accounts 50% to 60% of that total, or about 100 to 120 hours/month.
Savings, gains and benefits
By applying the estimated 30% to 70% time savings from using automation, the Managed Software module can reduce testing time by 30 to 80 hours each month. That’s roughly
the equivalent of 0.75 to 2 full-time IT staff, or between $4,700 and $12,500 each month.
The value is further increased by more consistent patching quality, shorter MTTRs and improved compliance metrics. IT staff also have more time to optimize existing processes and
handle new strategic projects. Companies using Managed Software also can increase their competitiveness when recruiting skilled IT staff.
A matter of value
Those are conservative and generalized estimates of the benefits, of course, and the actual metrics and results will depend on your particular circumstances. Even so, the potential ROI
makes the Managed Software module worthy of serious consideration by any current or prospective baramundi customer.
In the end, the decision to add Managed Software to the bMS comes down to value -- of a continuously improved cybersecurity posture, improved compliance in the face rising
threats, and of more effective use of IT staff time and costs.


