
Avoiding the security catch-22 of remote and WFH endpoint management
It’s a given that secure network connections are needed for protecting company infrastructure, keeping WFH and other remote users productive, and for managing their notebooks, smartphones and tablets. But the huge shift to remote computing earlier this year and the widespread use of VPNs has introduced a security catch-22 for IT admins.
The Catch of Remote Endpoint Management
Here’s the catch: what if the tools and procedures you use for ensuring network and endpoint security introduce security risks themselves? In other words, what’s the point of ensuring high-quality endpoint security if the process of maintaining that security requires either making remote device management harder, less frequent and more disruptive, or, drilling a hole in your central unified endpoint management (UEM) server?
The catch-22 comes with the use of VPNs. A simple and commonly used method is for the administrator to force a VPN connection to the endpoint being managed. However, doing so is not particularly user- or productivity-friendly. Many users do not need permanent VPN access for their daily work. So forcing a VPN connection to their device to install a patch or update tends to disrupt and annoy users and IT admins alike. It makes timely, reliable and consistent management of remote devices more difficult, which in turn can result in delayed or partial patching and updating and reduced security.
You could – theoretically -- access remote endpoints via the internet by placing the UEM server in the DMZ. But doing that not only violates the basic rules of IT security, it defies common sense. Needless to say, baramundi strongly advises against doing that!
Endpoint Managements via Gateway
The endpoint management system is one of the most security-critical elements in your network. It always has the highest administrative authorizations to enable IT staff to carry out the necessary endpoint management tasks. Whoever gains control of the management system can access and control virtually the entire network. That’s why the UEM server is shielded by a specially hardened component - the so-called gateway.
However, the default solution at some companies is to require the use of a VPN connection to connect the gateway to the remote endpoints. But then you’re right back to the catch-22 of securely managing endpoint security by adding security risks as well as headaches for users and IT staff.
There is a much better way!
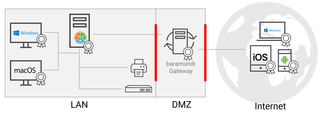
baramundi IEM (Internet enabled Endpoint Management) makes it possible to ditch the VPN-based management methods by establishing an encrypted channel between a management agent on each endpoint and the gateway. The end devices use this channel to communicate securely with the UEM server so that IT staff can install needed patches and updates, deploy endpoint software and monitor the status of each endpoint without compromising internal system security or disrupting users. A big advantage is that this channel is automatically established at device start-up -- even before the user logs on (i.e., neither you nor the user has to establish a VPN connection). This is done exclusively with encrypted, certificate-based authentication via standard SSL communication ports. It creates a connection that is independent of the stability and security of the user’s local network and, of course, the VPN.
Instead of relying on an insecure VPN workaround, we recommend using a well thought-out and secure UEM solution, namely the
baramundi Management Suite. You end up with the benefits of consistent, policy-based and reliable endpoint management without the headaches or the security catch-22.


