
Unified Endpoint Management for more security - And securely too?
Companies are good at protecting their IT infrastructure from attacks - both external and internal - as best they can. A reliable firewall solution, a reliable antivirus solution, as well as a reasonable backup & recovery strategy are part of the minimum equipment. In times of aggressive malware more than ever.
A secure UEM solution, what should I look for?
First of all, a secure UEM solution should be able to meet one's own requirements. It is particularly important not to be dazzled by the functional scope of the
various offerings. The focus should be on the secure operation of such a solution.
Here are a few tips:
- Question the security concepts behind such a solution. Ask the vendor about offers for training or guides for potential measures to harden the
systems.
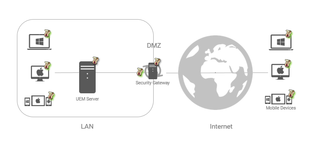
- Find out where the UEM system needs to be placed in the infrastructure and consider which relevant systems it needs access to.
- Do you want to use the UEM solution to manage mobile devices (smartphones, tablets, laptops) outside the company? Pay attention if the management
system must be placed in the DMZ for this purpose or direct port forwarding must be configured. Solutions such as the baramundi Management Suite rely on an abstraction layer that protects the management server from direct
attacks. The baramundi gateway ensures that only valid requests from known endpoints are forwarded and verified messages are sent to the management server so that
it can remain in the protected internal network.
- Take a look at securing the communication between the end device (mobile device, laptop, PC) and the controlling server.
Why does the secure operation of a UEM solution play a crucial role?
A UEM system is one of the most security-critical systems of all, because it has the highest administrative authorizations on the managed
endpoints. It also has direct access to connected active directories and issues certificates automatically via connected certificate authorities.
It is therefore all the more important that this system is protected as far as possible against unauthorized access. Whoever gains control over this system, then practically
automatically has the entire network under control as well.
Tips 1-3 strongly reinforce the need to secure the management system. But what if the communication between the managed endpoint and the server is the risk?
Common UEM solutions usually rely on encrypted communication between the endpoint and the server. This communication protection is identical to the usual encryption used when surfing the Internet with TLS protected connections.
However, this is not sufficient for trusted two-way communication at the client management level. Completely secure communication, in which both the server and the clients can uniquely identify their counterparts, can be achieved by additional cryptographic means. Therefore, you should place particular emphasis on tip 4. I would now like to show you what is important here.
Secure communication - what is important?
The following list describes some security features that distinguish a modern and secure UEM solution such as the baramundi Management Suite when communicating with the end devices:
- Use of secure certificates with at least 2048 bit key length and SHA-2 hash algorithm.
- Encrypted communication with TLS 1.2 or higher
- Authentication and authorization of endpoints using secure client certificates with at least 2048-bit key length and SHA2 hash algorithm
- Certificate pinning of managed endpoints on the server side and access control through appropriate "allow" lists
- Certificate pinning of the server on the client side
- Integrity checking of incoming messages based on digital signatures
- Easy replacement of corrupted certificates
- Consistent implementation for all managed endpoint types
Summary
With its range of functions, a modern UEM solution makes a significant contribution to increasing security in corporate infrastructures, but should not itself pose a security problem. With the baramundi Management Suite and its additional offerings, baramundi offers just such a UEM solution and clearly answers the initial question - secure for more security is possible.


