
Security for Windows endpoints: A holistic approach to updates and patches
Keeping current with Windows OS and applications updates and patches is, generally speaking, an essential practice to protect companies and users from cybersecurity threats. I say “generally” because the specifics of how IT managers keep up with and deploy updates and patches can mean the difference between secure and vulnerable network endpoint.
That can be a challenge for several reasons, including the frequency with which vendors release patches. While Microsoft has instituted regular semi-annual updates for Windows 10, patches
for the various third-party apps on your company’s endpoints might appear weekly depending on each vendor’s release schedule. Each new release poses the risk of either incompatibility with
existing installed software or can introduce unexpected vulnerabilities. That means IT managers have to take time to test patches on various endpoint configurations before deployment.
Another reason is the growing pressure on IT teams to keep endpoints up to date while minimizing system downtime. The shift to remote WFH computing and the use of VPNs has
only increased the difficulty of managing that.
Finally, you have to know in detail the current status and configuration of every endpoint.
That’s important to avoid introducing problems and to know if there are any faulty security configurations that need to be fixed ASAP.
So how do you as an IT admin stay on top of all of those and keep security holes closedwithout running yourself ragged?
A holistic approach in UEM
One of the key benefits of using a unified endpoint management (UEM) system like baramundi Management
Suite (bMS) is that it enables a holistic approach to OS installation, OS updates and other patch management functions.
Everything starts with the OS and Microsoft’s monthly cumulative Windows security patches. The bMS lets you deploy Microsoft patches automatically and at times you select. IT managers also
can automate nearly every detail of update and patch deployment as needed.
If you’re performing fresh OS installations there will necessarily be gaps between the stock OS image and any subsequent patches. That requires repetitive rework, and a
month or more can pass until the next patch deployment can be deployed. In addition, users’ home office PCs may not be configured for automatic updates or otherwise be set up according to
your company’s security policies.
How do you adapt the basic OS installation to your company’s specifications and preferences as well as meet the recommendations of federal cybersecurity
agencies like the CISA in the U.S. (Cybersecurity and Infrastructure Security Agency) or the BSI (Bundesamt für Sicherheit in der Informationstechnik) in Germany?
Closing the gaps
The baramundi OS customization tool makes it possible to customize Windows installation ISOs that integrate all cumulative OS updates within the installation. That ensures that any new Windows system is current and up-to-date. Even better, you’ll save a lot of time because you won’t have to go back and make a separate patch run to close the gap.
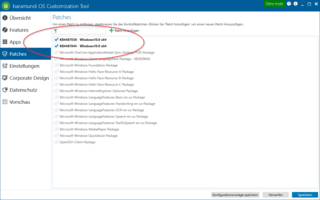
At the same time, you can configure security-related or other settings on the installation ISO, and, you can create as many customized ISOs as you need based on the variety of systems that you’re provisioning. That can include disabling Windows telemetry functions or Cortana, preventing users from synchronizing the clipboard on company computers with their home PCs, disallowing connection of external storage media and so forth. The OS Customization Tool has an extensive list of configuration options to match your needs and preferences.
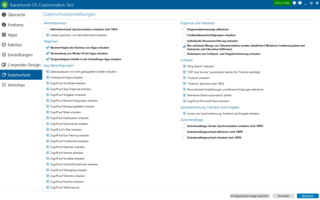
Once the operating system is installed you can address other important endpoint configuration questions like:
- Is an anti-virus program installed?
- What are user account access rights?
- What is the status of the firewall?
- Are all installed applications up to date?
- Is device storage encrypted?
All of that and more can be automatically, inventoried, viewed, reported and configured via the baramundi Management Suite.




